Why do websites get hacked?
In this article we explore the basics of website attacks, the motivation behind them, and some common ways in which attackers can get unauthorised access. This is not a technical article, and assumes no prior web security knowledge – it aims to provide an overview of the sort of website hacking that we see most often.
Anyone whose website has been hacked for the first time will want to know one thing: why would anyone want to hack my website? Many take such an attack personally and feel singled out. The truth is that your website is probably quite unremarkable. There’s nothing specific about you or your business which makes you a target. Any website is open to attack shortly after being made publicly available on the internet and yours is no different. If your website has been online for longer than a month, then chances are you’ve already been probed for potential attacks.
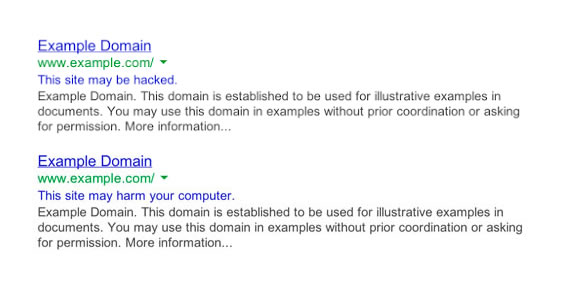
Are all attacks the same?
Attacks fit into two categories: targeted attacks, and automated attacks. You’re most likely to fall victim to the latter.
Targeted attacks are typically carried out against high profile targets and the attacker focuses their attention on a single website or company. These tend to involve a high level of skill, time and effort, often with greater reward.
For the majority of websites the attacks are completely automated. Your website is one of many on long lists of websites which will be targeted with automated tools and scripts. For an attacker, an automated approach significantly increases the chance of success by increasing the number of sites that can be attacked and reducing overhead and effort.
What’s the motivation behind attacks?
Website attacks are mainly carried out for financial gain. Although money is not the only motivation, it’s the rationale behind the vast majority of attacks on website such as yours. There are a number of ways hackers can make profit from your website:
Blackhat SEO
Blackhat SEO is a term used to describe malicious or aggressive techniques to influence search engine rankings. Your website can be used by an attacker to artificially increase the search engine rankings of other websites.
Google uses website links as an important search result ranking factor. The basic idea is that a website with useful information will be linked to from many other websites. The more links that website has, the more importance Google will grant it, and the higher it will rank in the search results.
Attackers can modify your website and create links to other unrelated external websites. The aim is to improve the search rankings of the target websites. These kinds of attacks often can go unnoticed by website owners as the links are usually discreet or even hidden to normal users.
Attackers may also redirect your visitors to other websites to increase their traffic. Sometimes these redirects target only certain visitors, making them difficult for website owners to spot.
Drive-by-downloads
Hackers can employ ‘drive-by-downloads’ – malicious files that a website sends to a browser for downloading. Typically this is malware intended to infect as many of your website visitors as possible. The exact purpose of malware differs drastically. Some malware will use infected computers to attack other websites. Other malware may steal credentials to email accounts or similar services. There are many different objectives of malware, but they will directly or indirectly increase revenue for the attacker.
Resource stealing
Your website may also be exploited for its resources. Once access has been gained to a website it can be used to attack and infect even more websites. More commonly, your website will be used to send large volumes of spam emails. As you might have guessed, these spam emails are usually aimed at infecting more computers and websites, or to earn more money by directing the recipients to ecommerce websites or affiliate revenue websites. Access to hacked websites can even be traded on parts of the “dark web”.
How do attackers gain access?
Attacks typically start with reconnaissance. Your website is publicly available on the internet and lots of important information about it can be easily obtained. Have a look at the following website to get a feel for the level of detail which is readily available for any given website: http://builtwith.com/castlegateit.co.uk
Information about software installed on your website is easy to obtain, and each piece of software is potentially exploitable. Attackers will learn about your content management system, themes, plugins and any utilities you have installed.
Automated tools are pointed at your website and begin to bombard you with payloads carefully crafted to exploit known security vulnerabilities in your website software. If your software is not up-to-date and patched against these vulnerabilities, the attackers may gain access.
Brute force attacks are also used to guess your username and password, so that the attacker may login to your content management system. Continuous automated attempts are made using common username and password combinations. If you’re using default username or a simple and insecure password you are inviting the attackers in, and giving them full control.

How can I stay protected?
Security is an extremely important consideration for website owners, but it’s often overlooked. The damage to traffic, reputation and trust resulting from your website being hacked is extremely bad for business. It often leads to a complete loss of traffic to your website and ultimately your website’s revenue. It’s unprofessional to say the least!
Keeping your software is up to date is one of the simplest things you can do to deter attackers. Although updates are important, there are many other important steps you can take to keep your website safe. Make sure you use an experienced and reputable web development company with the experience and technical knowledge required to keep you safe. A good developer will consider security throughout the build of your website, and not just bolt it on as an afterthought.
Ongoing security measures should be in place for any business-critical content managed website. It’s not enough to install a security plugin and leave it alone. Over time new features are added and new vulnerabilities are discovered, so periodic software updates and security reviews are critical.
If you don’t know what security measures your website has in place, you should contact your development company and find out what they are doing to protect you.

Related reading
At Castlegate IT we take security very seriously and have a strong track record in keeping our websites secure. WordPress is our content management system of choice and despite its reputation for being vulnerable to attacks; it’s very secure if used correctly. Its enormous popularity makes it a popular target for attackers.
Over the years new exploits have arisen and the types of attacks have changed, and so have we. We’ve put in place new procedures and security measures to protect our websites. We now offer a comprehensive security service to our clients to keep them safe.
We now take a number of extra steps to keep our clients safe. If you’d like to know the technical aspects behind what we do, you may read our technical article on how to keep WordPress secure to see the measures we put in place.
Want to know if your website is as secure as it should be? Get in touch and we’d be happy to talk to you about security.